There is no ‘one size fits all’ approach to Security Awareness. Since people are involved, it remains an ongoing challenge, but a worthy one. Not everyone is alike or cares about the same things, so it takes a multi-pronged, concerted effort, and a commitment to the journey to keep the program Engaging, Relevant, and Sustainable.
Part 1 of this series: Keeping Security Awareness Engaging.
Let’s start with a big picture reminder of the Cybersecurity Awareness Program journey.
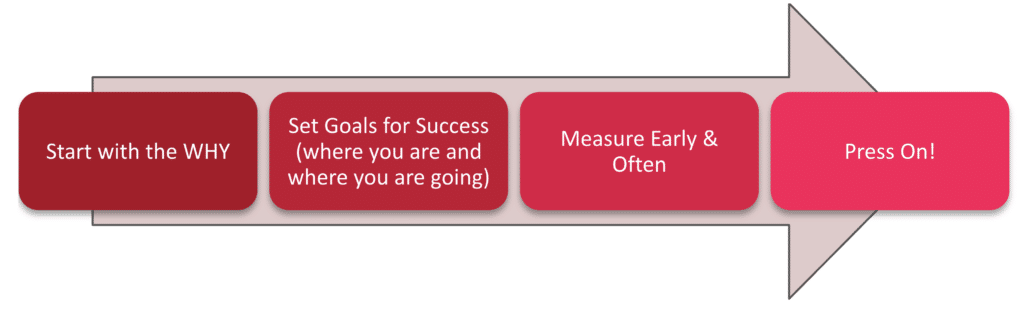
Notice that I’m calling this a PROGRAM… not a project. There is a difference. This journey has no foreseeable end but has a meaningful impact on the organization. It takes effort, considered thought, and a willingness to adjust as things change to keep the PROGRAM vibrant and meaningful.
Now let’s get into some practical ways to keep your PROGRAM Engaging.
Practical Ways to Keep Your Program Engaging:
- Engage THEM (the people in your organization). It seems like a simple start, but don’t assume you know what matters to them or what they are facing. In the words of Stephen Covey, ‘Seek first to understand, then to be understood.’ Here are some practical ways to engage the people in your organization:
- Engage each group and role in the organization.
- LISTEN with the intent to understand the issues each group faces and what matters to them.
- Meet them where they are by joining or being a part of existing groups and meetings. Don’t make them come to you.
- If you are not allowed to join some meetings, engage the leaders of each group to ASK them for information. Perhaps they may also be willing to convey questions or issues to the group and bring back feedback to you.
- Gather lessons learned, explanations, and opinions from people. Examples of feedback from staff at an organization:
- Keep it short (less than 15 minutes).
- We don’t read more than the first line or so of a paragraph (so adjust your communications accordingly).
- Educate your team to also LISTEN differently to information from people in the organization.
- Example: a Helpdesk staff made note and complained that someone asked them about a Gmail security question. When in fact, THIS IS GOOD. It means the caller was asking about Security hygiene issue and best practices. This was a teaching moment for the Helpdesk staff.
- Start from a place of trust
- The goal is NOT to catch people doing wrong. Don’t set traps and weaponize the results.
- Always convey that the goal of the program is to raise people’s security awareness and acumen …not send them to detention. If people think you are out to catch them making mistakes …they will stop listening.
- Your users want to do the right thing. Ask yourself, “how can you help?”
- Learn how to tell a negative story about your organization in a positive way.
- Things happen. Be open and transparent when addressing issues that the organization experiences.
- How you respond to an incident carries a lot of weight both inside and outside the organization.
- Reuse and leverage the story to promote good security best practices.
- Delivery / Engagement Tips:
- Keep regular messaging short, concise, and consistent.
- Remember the “Rule of 5-7” – people need to hear something 5-7 times before they realize they should pay attention. There’s more than just one way of communicating. Email is not your only avenue.
- Keep the messages immersive, but not disruptive – meaning get to the point and move on. People need to know three things: why they should care, what they need to know, and what they need to do.
- Think “Yes, AND …” there is no “one size fits all” approach.
- Equip Leadership – Help Leadership be successful in supporting Security Awareness by giving them talking points, notifying them of Security Awareness activities ahead of time, etc.
- Always look for creative ideas. Don’t think it all rests on your creativity.
- Crowd source from your organization.
- Ask peers.
- Leverage industry groups.
- Don’t be afraid to ask for help (Marketing Department, trusted business partners, etc.).
- Some Additional Ideas to keep people engaged:
- Drawings / raffles
- Steady flow of practical tips for home and personal security
- Make it a part of the organization’s HR review process
- Tie it to the organization’s and individual’s ethical behavior
Next in the series will be Part 2: Keeping Security Awareness Relevant followed by Part 3: Keeping Security Awareness Sustainable. If you need help getting your security awareness efforts off the ground or achieving all three of the above-mentioned goals with your security awareness program, we’re here to help.

Kenny Leckie
Alterity | Senior Technology & Change Management Consultant
In his role as Senior Technology and Change Management Consultant, Kenny provides thought leadership and consulting to the community in areas of information security/cybersecurity awareness, change management, user adoption, adult learning, employee engagement, professional development, and business strategy. He also works with clients to develop and deploy customized programs with an emphasis on user adoption and increased return on investment. Kenny is a Prosci
Certified Change Practitioner, a Certified Technical Trainer and has earned the trust of organizations across the US, Canada, The UK, Europe and Australia.
Kenny has more than thirty years of combined experience as a Chief Information Officer, Manager of Support & Training, and now a consultant, providing him a unique point of view and understanding of the challenges of introducing change in organizations. He combines his years of experience with a strategic approach to help clients implement programs that allows focus on the business while minimizing risk to confidential, protected, and sensitive information. Kenny is an author and speaker and a winner of ILTA’s 2018 Innovative Consultant of the Year.




